Types of hacking
- DDOS
- Fileless virus
- Trojan Horse
- Password
- Phishing
- Ransomware
- SQL injection
- Code injection
- DNS hijacking
- Spyware
- AdWare
- Botnets
- Bruteforce attack
- Worms
- Man in the middle
- URL hijacking
- XSS attack
- Idor attack
- Zero-day Attack Hats
Networking
Computer networking enables devices and endpoints to be connected to each other on a local area network (LAN) or to a larger network, such as the internet or a private wide area network (WAN). This is an essential function for service providers, businesses and consumers worldwide to share resources , use or offer services, and communicate. Networking facilitates everything from telephone calls and text messaging to streaming video and the internet of things (IoT).Hackers use networking maliciously they can hack into different systems on a network and gather sensitive information and encrypt certain functions.
Pentesting
Penetration testing (or pen testing) is a security exercise where a cyber-security expert attempts to find and exploit vulnerabilities in a computer system. The purpose of this simulated attack is to identify any weak spots in a systems defenses which attackers could take advantage of. This is like a bank hiring someone to dress as a burglar and try to break into their building and gain access to the vault. If the 'burglar' succeeds and gets into the bank or the vault, the bank will gain valuable information on how they need to tighten their security measures.Pentesting is an essential part of ethical hacking its used to identify any weakness of a company's network and physical security also.
Red Teaming
Red teams are ethical hacker who help test an organization's defenses by identifying vulnerabilities and launching attacks in a controlled environment. Red teams are opposed by defenders called blue teams, and both parties work together to provide a comprehensive picture of organizational security readiness.When a company/organization has there ethical hackers doing defensive work and offensive security they are known as the purple team.
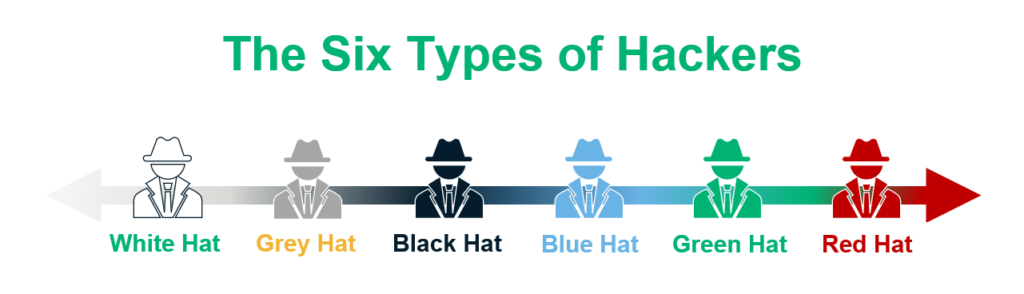
Hats
In hacking we have different terms for different types of hackers and we refer to these hackers as hats with different colors for example a white hat would be someone who uses hacking for a good purpose and works for a legitamet company. The opposite of a white hat would be a black hat which uses hacking maliciously.


Want to become a hacker ?
-If you want to become an ethical hacker there are some skills that you will have to learn, here are just some of them.
- Networking
- Kali Linux
- Scripting
- digital forensic analysis
- Programing
- Hardware knowledge
- Cryptography
- Reverse Engineering